Tunneling
SSH Tunnels
- Disabling SSH DNS lookup on redirector boxes can greatly speed up the response time and speed through the chain
ssh user@hop1 -NfL lport1:hop2:hop2portFrom SSH sessions:
~C # Drops into SSH command line
-L[bind addr]:<port>:<forward addr>:<port> # Add a forward tunnel
-KL:<port> # Remove a forward tunnel
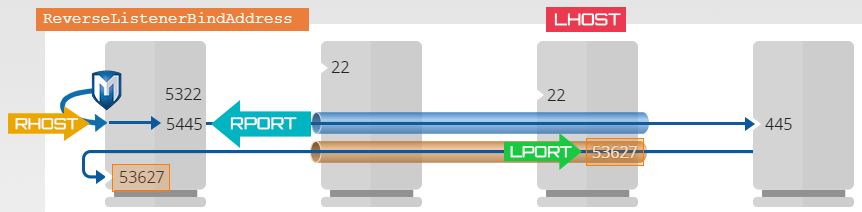
-R<port>:<forward addr>:<port> # Add a reverse tunnel
-KR:<port> # Remove a reverse tunnel
~# # List forwarded connectionsSSH Proxy Tunnel
ssh user@127.0.0.1 -p tunnel_port -NfD proxy_portForward SSH Tunnels
- Create first tunnel
ssh <user>@<firsthop> -NfL <lport1>:<nexthop>:<rport>- Tunnel through previous, continue to chain to add more hops to the route
ssh <user>@localhost -p <lport1> -NfL <lport2>:<nexthop>:<rport2>Reverse SSH Tunnels
By default reverse tunnels listen globally on all interfaces Configuring a reverse tunnel does NOT start a listener on the local machine
Sends all traffic received on remote host’s rport to your localhost’s lport
ssh <user>@<target> -NfR <rport>:localhost:<lport>SSH control sockets
- Create the socket
ssh -M -S /tmp/<name> <user>@<ip>- Use a socket
ssh -S /tmp/<name> thispartisignoredbutrequired@127
scp -o ControlPath=/tmp/<name> thispartisignoredbutrequired@127:<file> <dest>